As the use of digital technology to support daily personal and professional needs increases in human life today, cybersecurity awareness becomes more important than ever before. We are increasingly vulnerable to cyber threats and attacks. The types of cyber-attacks carried out by cyber criminals are becoming even more sophisticated, particularly in attacking devices, networks, and stealing our data without us even realizing it. Consequently, having a thorough comprehension of cybersecurity and the possible risks that we encounter on a daily basis is extremely important.
Moreover, as our reliance on cyberspace grows and we become more immersed in online activities, the prevalence of cyberthreats becomes an ever-present reality. Cyberspace has emerged as a dynamic realm where business activities, social interactions, and most notably, social relations are forged. The shift towards conducting various aspects of our lives in the digital realm exposes us to potential risks and vulnerabilities that we must remain vigilant against. This article will discuss fundamental knowledge about cybersecurity that is essential to be aware of.
Cyberthreats and Cyberattacks
The issue of cybersecurity encompasses various aspects. It is a concern for defense and governmental security, businesses, organizations, and individuals alike. We can see that the field of cybersecurity is closely intertwined with discussions related to state defense and security. Exploring the domain of cybersecurity reveals a wealth of search results and online conversations centered around this topic. High-profile events along with the Stuxnet assault and the notorious data breach associated with Edward Snowden all contribute to the increasing recognition of the essential position played with the aid of cybersecurity in safeguarding nations and their assets.
Other example, inside the corporate zone, corporations depend heavily on secure networks, information safety measures, and strong cybersecurity protocols to safeguard their touchy records, highbrow assets, and financial transactions from unauthorized get right of entry to or cyberattacks. Additionally, healthcare institutions face cybersecurity demanding situations in protective patients’ clinical statistics and ensuring the confidentiality of touchy healthcare records. Furthermore, character users are susceptible to threats which includes identification theft, on-line scams, and privateness breaches, highlighting the importance of cybersecurity in personal online activities. These examples display that cybersecurity pervades all aspects of our cutting-edge virtual lives, necessitating a comprehensive technique to mitigate risks and shield against cyber threats.
According to Andreasson (2012), cyberthreats can be categorized in two ways, as politically motivated and the non-political one. Politically motivated cyberthreats can be defined as cyber warfare, cyber terrorism, espionage, and hacktivism. Meanwhile, the non-political cyberthreats might have several motives such as financially motivated (cybercrime, intellectual property, theft, and fraud), or even it is just for fun or retribution purpose. In this context, it can be viewed that cyberspace with its vulnerability to threats has a complex and multifaceted context to our very own life, and everyone, whether it is state or non-state actors in cyberspace is typically vulnerable and at risk to any of threats or attacks.
In the domain of cybersecurity, there exists a multitude of terms and concepts, among them being cyber threats and cyberattacks. While these terms are related, they have distinct meanings. To begin with, Li and Liu (2021) has summarized some basic definitions and concepts of cyberspace in their article. According to Li and Liu (2021), cyberthreat refers to an event wherein an information system is exploited through unauthorized access, destruction, disclosure, alteration of information, or disruption of service delivery, posing potential harm to missions, tasks, reputation, national cyber assets, or individuals. When unauthorized cyber acts breach the security policy of a cyber-asset, causing damage, disruption, or interference with services or information access linked to the targeted national cyber asset, they are classified as cyber-attacks. Furthermore, intentionally using a cyber-weapon to trigger a cyber-incident on an information system also falls under the category of cyber-attacks. Based on the given explanation, it becomes apparent that the distinctions between these two terms lie in their intentional aspect to cause damage and how they are defined. Cyberthreats are characterized by their representation of potential risks and events, while cyberattacks are defined by their primary objective of causing damage.
Cyberspace faces multiple threats such as foreign intelligence services, financial-driven attacks, hackers, hacktivist groups, internal dissatisfied agents, and terrorists (Li & Liu, 2021). These threats target information infrastructures, infiltrate networks, and aim to destroy vital infrastructure, weaken economies, and undermine national security. See Fig. 1 for an illustration of threats in cyberspace.
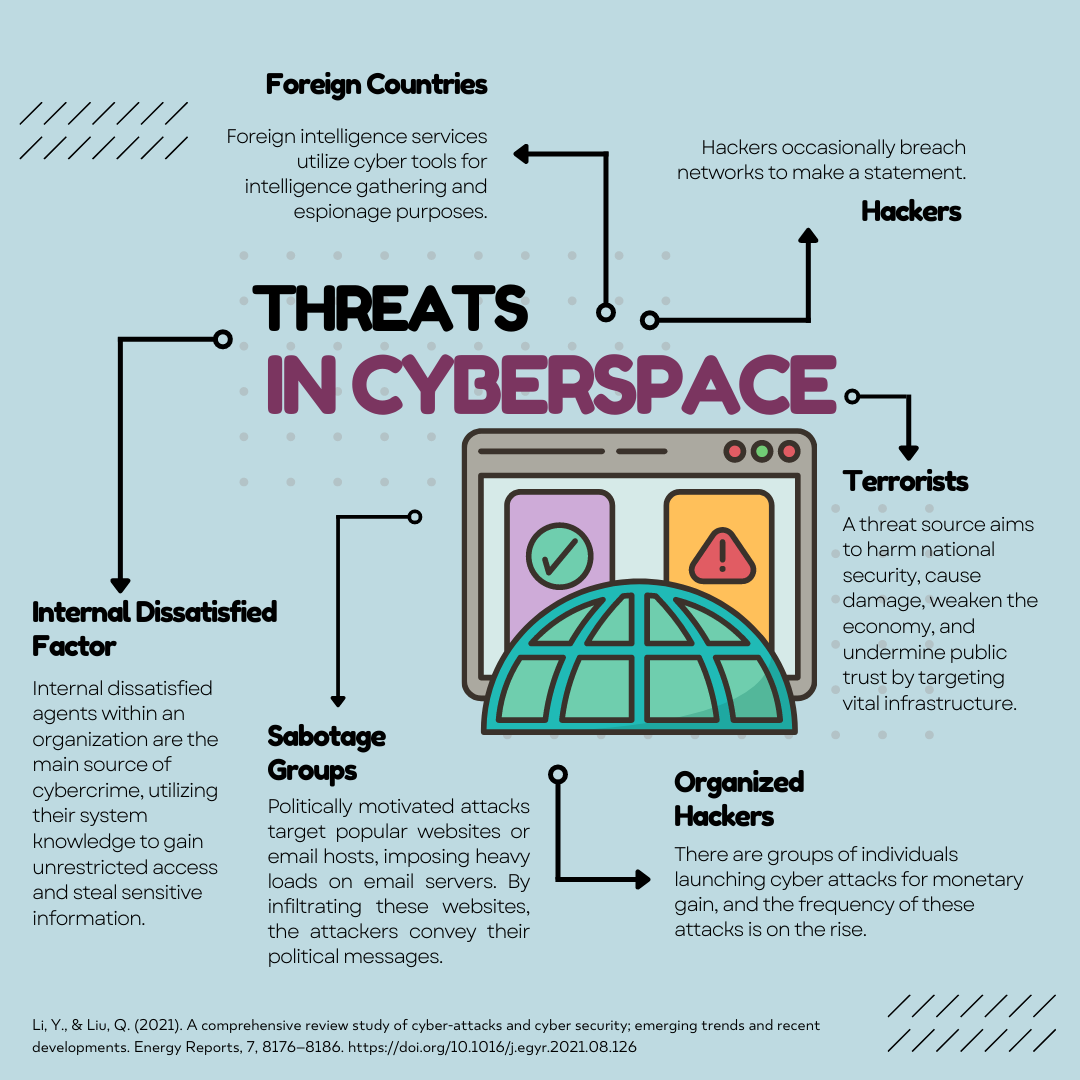 Fig. 1. Threats in Cyberspace
Fig. 1. Threats in Cyberspace
Besides, important cyber-attack methods include Denial of Service, logical bomb, Abuse tools, Sniffer, Trojan horse, Virus, Worm, Send spam, and Botnet (Li & Liu, 2021). Denial of Service disrupts authorized access to a system by flooding it with messages. Widespread Denial of Service involves simultaneous attacks from multiple distributed systems. Abuse tools detect and exploit network vulnerabilities. A logic bomb triggers destructive actions based on specific events in a program. Sniffer eavesdrops on data streams to find specific information. Trojan horse disguises harmful code as a helpful program. Viruses infect system files, while worms self-replicate across networks. Botnets are networks of infected systems used for malware distribution, attacks, and spam.
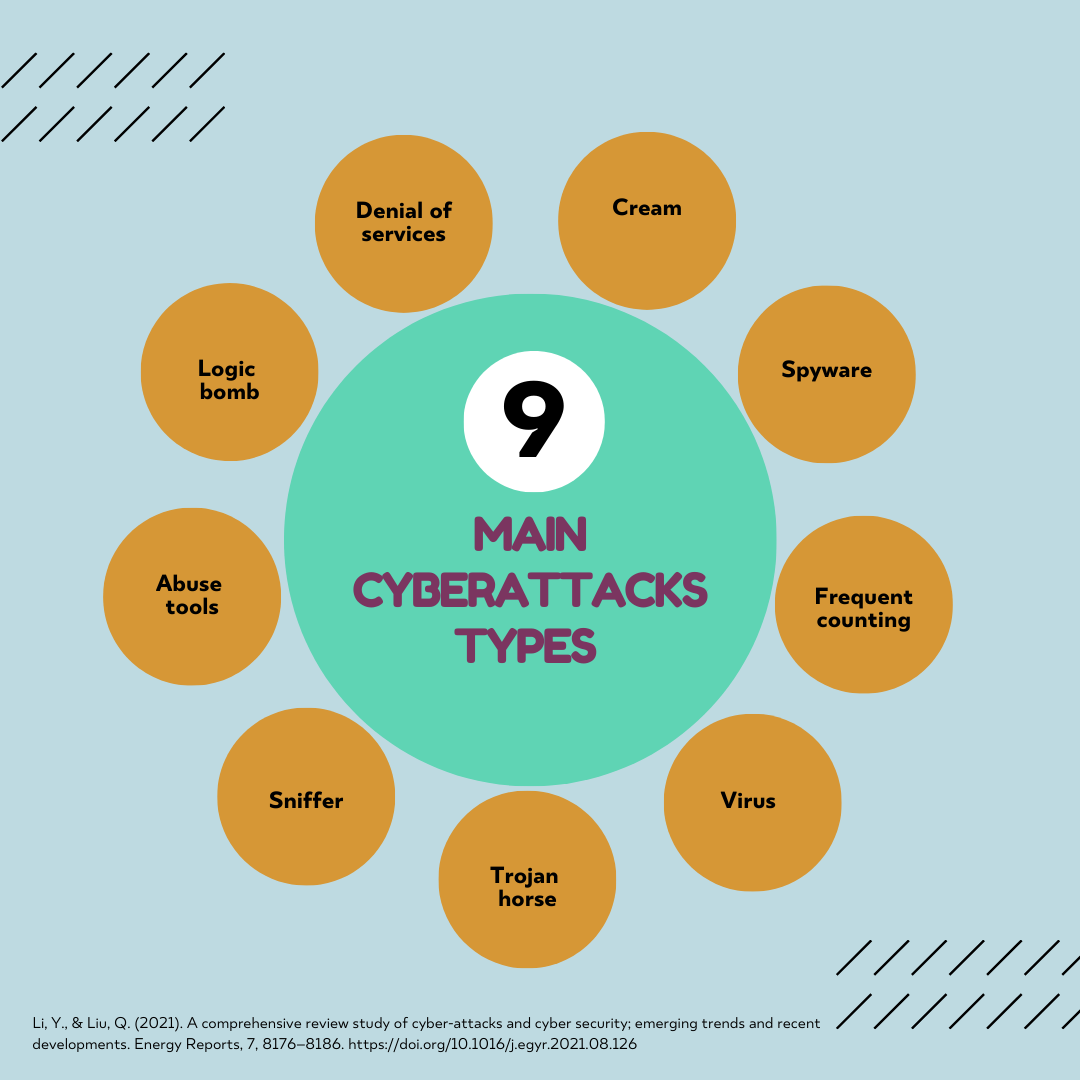 Fig. 2. Main Cyberattacks Types
Fig. 2. Main Cyberattacks Types
Cybersecurity and Its Types
Regarding security itself, according to Singer & Friedman (2014), security goes beyond mere freedom from danger and involves the presence of an adversary. Therefore, a cybersecurity problem arises only when an adversary aims to benefit from their actions, such as acquiring sensitive data, undermining systems, or obstructing legitimate use. Enhancing cybersecurity consequently is becoming more important than ever before.
Cybersecurity is a proactive practice that encompasses sensible measures to guard statistics, networks, and records from each internal and external threats. It includes the knowledge of cybersecurity experts who are accountable for safeguarding networks, servers, intranets, and computer systems (Li & Liu, 2021). The main goal of cybersecurity is to prevent unauthorized get entry to and shield against malicious assaults on diverse digital systems, together with computer systems, servers, cellular devices, networks, and data. It is likewise known as information technology security or the protection of electronic information (Gulhane & Manwar, 2021).
Apart from that, Li & Liu (2021) also mentioned that there are several types of efforts in implementing cybersecurity enhancements, such as infrastructure security, cloud security, network security, application security, information security, end-user training, and data security prevention.
The more activities we engage in cyberspace, the more vulnerable we become to threats and attacks. Although certain actors such as industries, governments, and public figures may be more susceptible, it is also important to acknowledge that none of us are truly safe in this cyberspace. This is also due to the fact that our personal information is collected by both the government, corporations, and organizations as well. If these private details are exposed, it can result in detrimental outcomes.
The Importance of Cybersecurity and Its Awareness Building
Cybersecurity is crucial as it helps individuals and organizations to defend themselves from cyber threats and attacks. Cyber threats and attacks can purpose full-size damage to both individuals and companies, together with financial loss, reputational harm, and legal results. Furthermore, the ever-changing nature of cybercrime poses challenges for individuals and organizations to stay abreast of the latest vulnerabilities and threats.
Following are the Importance of Cybersecurity according to geeksforgeeks:
- Protecting Sensitive Data
Protects valuable data from unauthorized access and theft.
- Prevention of Cyber Attacks
Malware infections, ransomware, phishing, and Distributed Denial of Service (DDoS) attacks can severely disrupt businesses and individuals. Effective cybersecurity measures help prevent such attacks, reducing the risks of data breaches, financial losses, and operational disruptions.
- Safeguarding Critical Infrastructure
Interconnected computer systems support critical infrastructure, including power grids, transportation systems, healthcare systems, and communication networks. Guarding these systems against cyber threats is crucial to ensure uninterrupted essential services and prevent potential disruptions that could impact public safety and national security.
- Maintaining Business Continuity
Cyber attacks can significantly disrupt businesses, leading to revenue loss, reputational damage, and even business closures. Cybersecurity measures help maintain business continuity by preventing or minimizing the impact of such attacks.
- Compliance with Regulations
Non-compliance with regulations mandating the protection of sensitive data in various industries can lead to substantial fines and legal consequences. Cybersecurity plays a vital role in ensuring compliance with regulations like HIPAA, GDPR, and PCI DSS.
- Protecting National Security
Cyberattacks targeting critical infrastructure, government systems, and military organizations can compromise national security. Cybersecurity plays an important role in protecting national security and preventing cyber warfare.
- Preserving Privacy
Cybersecurity is crucial for preserving privacy, by protecting personal data from unauthorized access, surveillance, and misuse, cybersecurity upholds individual’s privacy rights and fosters trust in digital services.
While cybersecurity is undoubtedly valuable in practice, it is not exempt from encountering various challenges. Nevertheless, the significance of raising cybersecurity awareness cannot be undermined. It enables individuals and organizations to stay informed about the latest developments in the field, encompassing emerging threats and vulnerabilities. By maintaining awareness of these potential risks, individuals and organizations can adopt suitable measures to safeguard their data and interests. These precautions may entail implementing robust passwords, regularly updating software, and remaining vigilant when encountering suspicious emails or messages. Apart from that, Irei in her article in TechTarget, mentioned some important ways to protect yourself and your organizations from cyberthreats and attacks by maintaining cyber hygiene. Following are some best practices according to TechTarget:
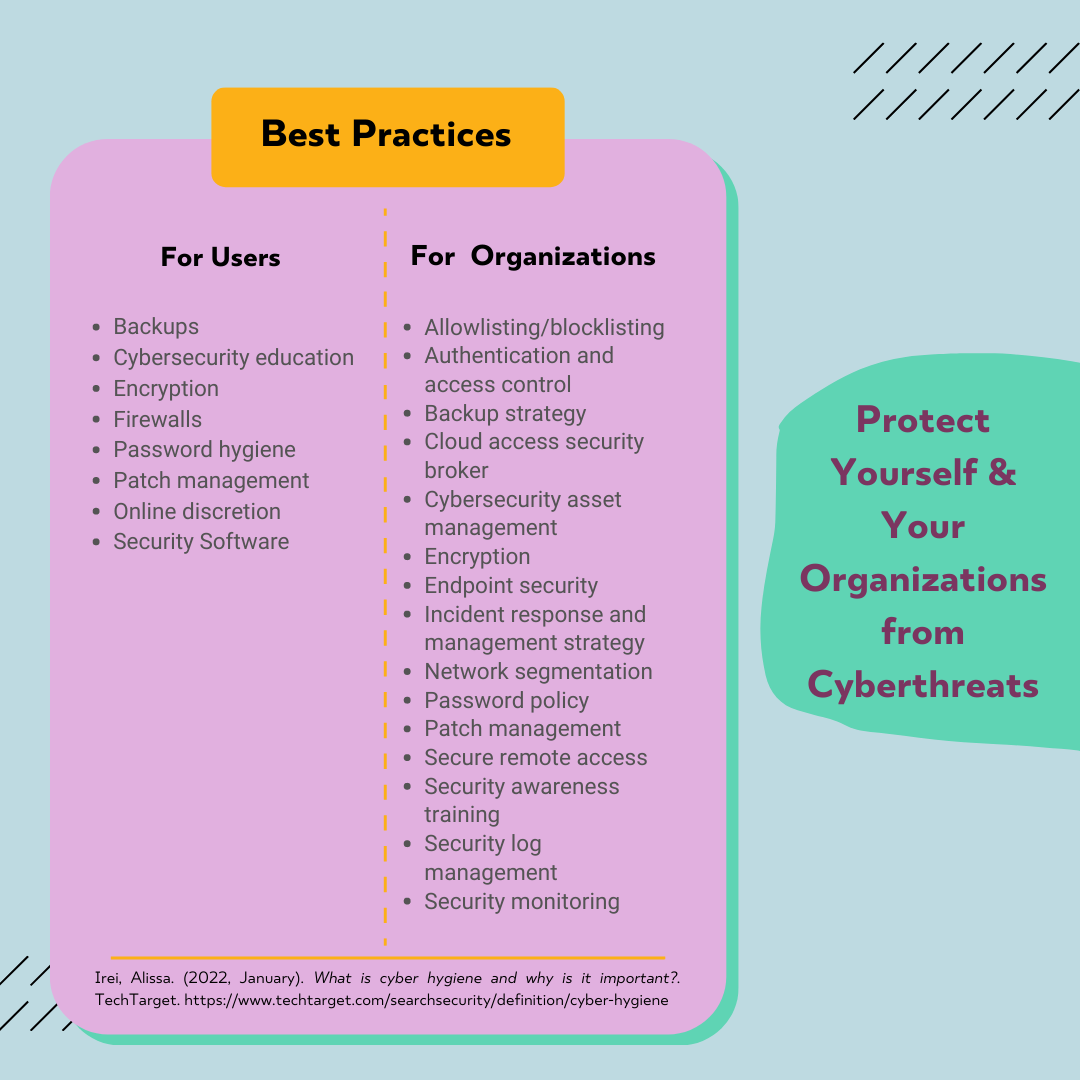 Fig. 3. Best Practices to Protect from Cyberthreats
Fig. 3. Best Practices to Protect from Cyberthreats
Conclusion
To summarize, cybersecurity has become increasingly important in our modern technological age. It plays a role as an essential safety net for individuals and organizations, protecting us from cyberthreats, and keeping us abreast of the latest trends in cybersecurity. By implementing the aforementioned tips you can enhance your online security and sensitive information against the ever-present threat of cyber criminals. It is important to emphasize that cyber security is a collective responsibility. Governments have a pivotal role to play in formulating policies that prioritize the safeguarding of both citizen data and national cybersecurity. Simultaneously, corporations bear the responsibility of ensuring the protection of data within their purview. Additionally, in creating a safe and secure cyberspace environment for all is also requiring each individual actively participates.
References:
Andreasson, K. (2012). Cybersecurity; Public Sector Threats and Responses. Boca Raton: CRC Press.
Cyber Security, Types and Importance. (2023, May). Geeksforgeeks. https://www.geeksforgeeks.org/cyber-security-types-and-importance/
Gulhane and Manwar. (2021). Introduction to Cyber Security – A Review. International Journal of Scientific Research in Science and Technology, 8(6), 484-487.
Irei, A. (2022). What is cyber hygiene and why is it important?. TechTarget. Retrieved from https://www.techtarget.com/searchsecurity/definition/cyber-hygiene
Li and Liu. (2021). A comprehensive review study of cyber-attacks and cyber security; Emerging trends and recent developments. Energy Reports,7, 8176–8186.
Singer and Friedman. (2014). Cybersecurity and Cyberwar; What Everyone Needs to Know. United States of America: Oxford University Press.
Note: This article was written by Viona M/ Junior Research Fellow – R4D Unit of the Development CAFE, the views are author’s own and does not necessarily reflect The Development CAFE’s official position, rather only as an information piece.

